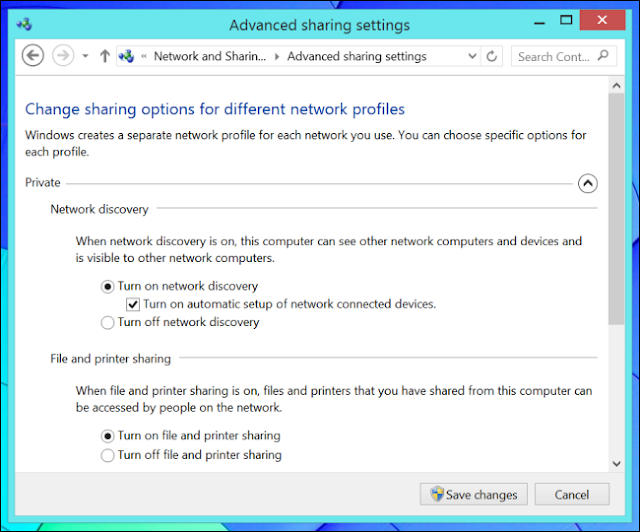
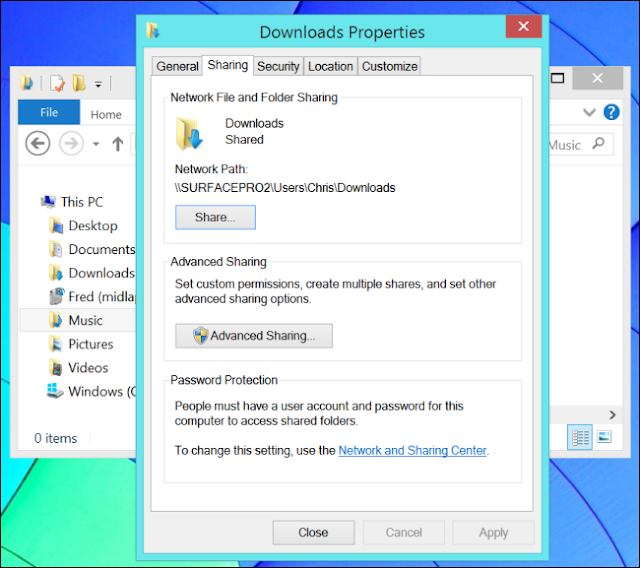
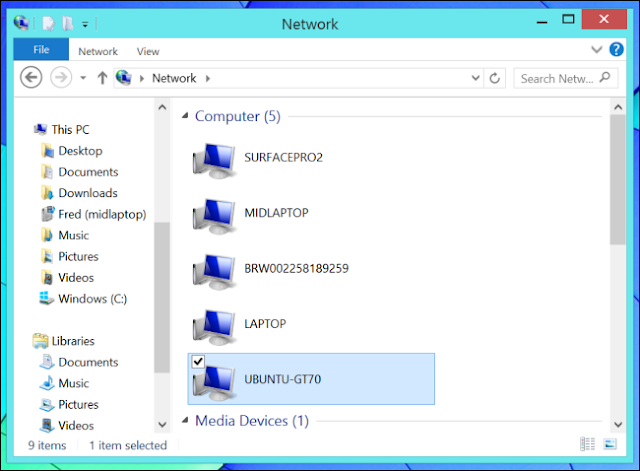
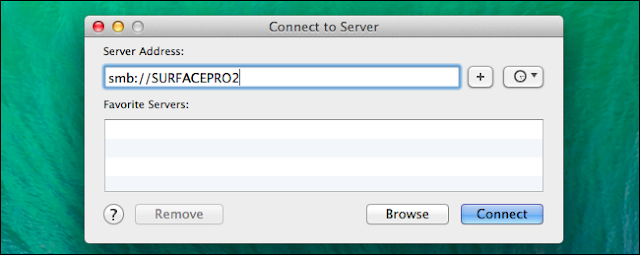
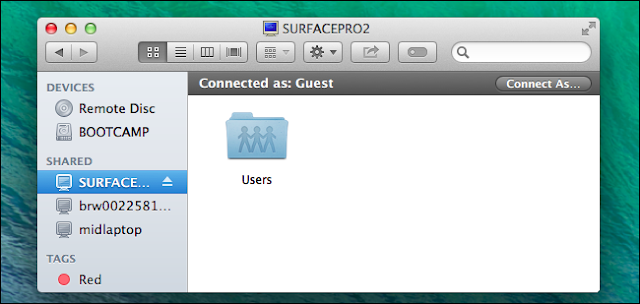
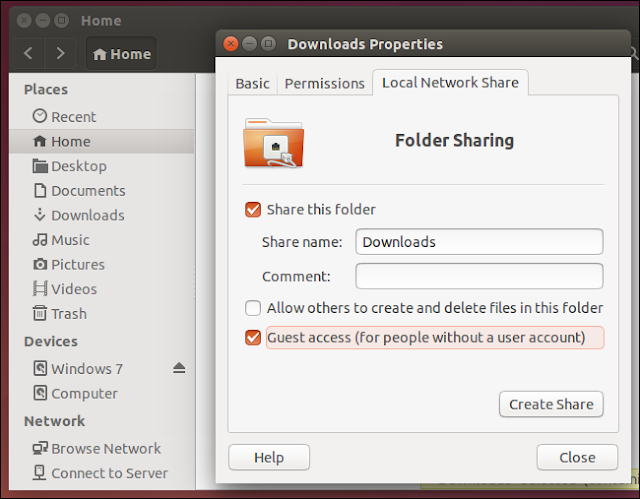
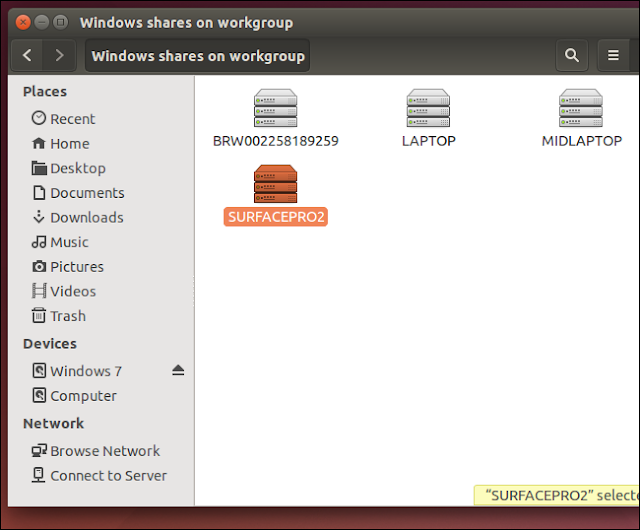
Some NETGEAR products confirm to the IEEE 802.11g standard for wireless LAN (WLANs). On an 802.11 wireless link, data is encoded using DSSS technology and it transmitted the radio spectrum at 2.5 GHz. Maximum data rate is 54 mbps, when the radio signal is weak or when interference is detected. With a wireless access point, the wireless LAN can operate in the infrastructure mode. This mode lets you connect wirelessly to wireless network devices within a fixed range or area of coverage. The access point has one or more antennas that allow you to interact with wireless nodes. In infrastructure mode, the wireless access point converts airwave data into wired Ethernet data, acting as a bridge between the wired LAN and wireless clients. Connecting multiple access points via a wired Ethernet backbone can further extend the wireless network coverage. As a mobile computing device moves out of the range of one access points it moves into the range of another. As a result, wireless clients can freely roam from one access point domain to another and still maintain seamless network connection.

In an ad hoc network, computers are brought together as needed; thus, the network has no structure or fixed points—each node can be set up to communicate with any other node. No access point is involved in this configuration. This mode enables you to quickly set up a small wireless workgroup and allows workgroup members to exchange data or share printers as supported by Microsoft networking in the various Windows operating systems. Some vendors also refer to ad-hoc networking as peer-to-peer group networking. In this configuration, network packets are directly sent and received by the intended transmitting and receiving stations. As long as the stations are within range of one another, this is the easiest and least expensive way to set up a wireless network.
Introduction to Wi-Fi
Wi-Fi, also spelled Wi-fi or Wi-Fi, is a local area wireless technology, which allows an electronic device to exchange data or connect to the internet using 2.4 GHz UHF and 5 GHz SHF radio waves. According to the Wi-Fi Alliance Wi-Fi as any "wireless local area network (WLAN) products that are based on the Institute of Electrical and Electronics Engineers' (IEEE) 802.11 standards". Moreover, since most modern WLANs are based on these standards, the term "Wi-Fi" is used in general English as a synonym for "WLAN". Only Wi-Fi products that complete Wi-Fi Alliance interoperability certification testing successfully may use the "Wi-Fi CERTIFIED" trademark.

Many devices can use Wi-Fi, like personal computers, video-game consoles, smartphones, some digital cameras, tablet computers and digital audio players. These devices can be connected over a network resource such as the Internet via a wireless network access point. Such as an access point (or hotspot) has a range of about 20 meters (66 feet) indoors and a greater range outdoors. Hotspot may have the coverage area as small as a single room with walls that block radio waves, or as large as many square kilometers achieved by using multiple overlapping access points. Wi-Fi are the less secure than wired connections (such as Ethernet), as an intruder does not need a physical connection. Web pages that use SSL are secure but unencrypted internet access can easily be detected by intruders. Due to this reason, Wi-Fi has adopted various encryption technologies. The early encryption WEP, proved easy to break. Higher quality protocols (WPA, WPA2) were added later. An optional feature added in 2007, called Wi-Fi Protected Setup (WPS), had a serious flaw that allowed an attacker to recover the router's password. The Wi-Fi Alliance has since updated its test plan and certification program to ensure all newly certified devices resist attacks.
WEP or Wired Equivalent Privacy is the most common standard for wireless encryption and it is proven that it can be easily broken even when it is properly configured. Usually Wi-Fi access points are configured using an open/ encryption- free mode. This zero-configuration device which is out-of-the-box ready to use is beneficial for novice users but since it is the default mode, it offers zero wireless security. In order to turn on the security, users are required to configure this device with the help of GUI (Graphical User Interface) software. A major security concern in unencrypted Wi-Fi networks is that it enables users to monitor and record personal information of all users who are using this network. Such networks are required to be secured with the help of other protection methods, such as Hypertext Transfer Protocol over HTTPS (Transport Layer Security) and VPN. This security concern is overcome with the help of WPA2 if a strong passphrase is used to secure the network.
US Federal Communications Commission released the 802.11g wireless fidelity for the ISM band for unlicensed use. In 1991, NCR Corporation with AT&T Corporation invented the precursor to 802.11 intended for use in cashier systems. The first wireless products were under the name WaveLAN.

Some have dubbed Dutch engineer Vic Hayes the "father of Wi-Fi" due to his involvement in negotiating the initial standards within the IEEE while chairing the workgroup. The Australian radio-astronomer John O'Sullivan developed a key patent, which was used in Wi-Fi as a by-product in a CSIRO research project, "a failed experiment to detect exploding mini black holes the size of an atomic particle". In 1992 and 1996, Australian organization CSIRO (the Australian Commonwealth Scientific and Industrial Research Organization) obtained patents for a method later used in Wi-Fi to "unsmear" the signal. In 1999, the Wi-Fi Alliance formed as a trade association to hold the Wi-Fi trademark under which most products are sold.
UPDATES OF WI-FI: WI-MAX
After the past three decades after invention of Wireless system, we were unable to send data without any wire at high speed. In 1999, the invention of Wi-Fi revaluated the telecom industry. The latest version of Wi-Fi 2004.802.16d, started to update the Wi-Fi system. Wi-MAX (Worldwide Interoperability for Microwave Access) is a wireless communications standard designed to provide 30 to 40 megabit-per-second data rates, with the 2011 update providing up to 1 Gbit/s for fixed stations. The name "Wi-MAX" was created by the WiMAX Forum, which was formed in June 2001 to promote conformity and interoperability of the standard. The forum describes Wi-MAX as "a standards-based technology enabling the delivery of last mile wireless broadband access as an alternative to cable and DSL".

Wi-MAX refers to interoperable implementations of the IEEE 802.16 family of wireless-networks standards ratified by the Wi-MAX Forum. (Similarly, Wi-Fi refers to interoperable implementations of the IEEE 802.11 Wireless LAN standards certified by the Wi-Fi Alliance.) Wi-MAX Forum certification allows vendors to sell fixed or mobile products as Wi-MAX certified, thus ensuring a level of interoperability with other certified products, as long as they fit the same profile. The original IEEE 802.16 standard (now called "Fixed Wi-MAX") was published in 2001. Wi-MAX adopted some of its technology from Wi-Bro, a service marketed in Korea.
Worldwide Interoperability for Microwave Access (Wi- MAX), is a wireless communications technology aiming to provide wireless data over long distances in a variety of ways as an alternative to cable and DSL, from point-to-point links to full mobile cellular type access. It is based on the IEEE 802.16 standard. The name Wi-MAX was created by the Wi-MAX Forum, which was formed in June 2001 as an industry-led, not- for-profit organization to promote conformance and interoperability of the standard. The goal of this deliverable is to provide an overview of the functionality and a description of the Wi-MAX network architecture. The coexistence and interoperability solutions between Wi-MAX and other wireless access networks, such as WLAN (IEEE 802.11) in Beyond 3G (B3G) networks.
NEW INTERNET TECHNOLOGY: LI-FI
Weather we are using the wireless connection in a coffee shop or stealing it from the guy next door, or competing bandwidth at a conference or training centers, we get frustrated for the slow speed of internet. Thirty years after the introduction of the first commercially available mobile communication systems, wireless connectivity has become the essential commodity like gas and electricity. But in the contradiction, the limited available RF spectrum in subject to think about the problems which are faced mentioned before. Motivated by the looming radio frequency (RF) spectrum crisis, the scientists demonstrated that owe has now reached a state where it can demonstrate that, it is a variable and matured solution to this fundamental problem in particular, in case of the indoor communications, where most mobile data & traffic is consumed.

Li-fi is the only solution which is operated via VLC. Therefore, there have been many independent warnings of a looming. 'RF Spectrum Crisis ' as a mobile data demands continue to increase while the network spectral efficiency saturates despite newly - introduced standards and great technologies advancements in the field. It is new estimated that by 2017, more than 11 bytes of data traffic will have to be transferred through mobile networks every month.
SIGNAL MODULATION IN OWC:
Seamless all own would require the ubiquitous coverage provided by the optical front- end elements. This the usage of a large amount of Li-fi, enable lightning units. The most likely candidates for front end devices in VLC are incoherent solid-state lighting LED‘S due to their low cost. Due to the physical properties of these compounds, information can only be encoded in the intensity of emitted light.
MULTIPLE ACCESSES:
A networking solution cannot be realized without any suitable multiple access scheme that allows multiple users to share the communication resources without any mutual cross talk. Multiple access schemes used in RF communication can be adopted for OWC as long as the necessary modification related to the 1M/DD nature of modulating signals, are performed of DM come with of DMA . Single carrier modulation schemes such as M- PAM, OOK, PWM, and CDMA.
HOW LI- FI WORKS:
We can imagine ourselves walking into a complex where GPS Signals are unavailable but the complex is equipped with ceiling bulbs that create their own ' constellation ' of navigation becomes. As the concern of our cell phone automatically receives these signals, it switches our navigation software to use this information to guide us to the ATM machine we are looking for we conclude our ATM transaction and notice the Giga spot sign for instant digital movie download within a few seconds, or AD movie into Gign link flash desire plugged into the USB port of our smartphone. As we walk away, out phone notifies us that the leather jacket featured in the character of movie is ON sale nearby. We walk over there towards the slow window and own image comes up on the screen, wearing the jackets. We can turn and pause while the image matches our orientation and body gestures for a digital filtering. When we walk into the store, the clerk handover us the actual jacket into exactly size tilting.

Security Concerns:
It is a proven fact that Li-Fi is more secure as compared to traditional Wi-Fi. This is because Wi-Fi routers are generally used by attackers to enter a network and strong firewalls are also unable to safeguard your network from these attackers. One of the common reasons behind this is that the range of Wi-Fi routers is an important factor which enables these security breaches into your Wi-Fi network. On the other hand, Li-Fi uses light which limits the range of the internet connection and it cannot be increased at any cost. Thus, not letting the bulb be lightened or dimmed manually. This peculiar feature of Li-Fi will protect your network from interference from your neighbours.
FUTURE OF LI-FI: INTRODUCTION TO GI-FI
Gi-Fi or gigabit wireless refers to wireless communication at a data rate of more than one billion bits (gigabit) per second. By 2004 some trade press used the term "Gi-Fi" to refer to faster versions of the IEEE 802.11 standards marketed under the trademark Wi-Fi. In 2008 researchers at the University of Melbourne demonstrated a transceiver integrated on a single integrated circuit (chip) that operated at 60 GHz on the CMOS process. It will allow wireless transfer of audio and video data at up to 5 gigabits per second, ten times the current maximum wireless transfer rate, at one-tenth the cost. Researchers chose the 57–64 GHz unlicensed frequency band since the millimeter-wave range of the spectrum allowed high component on-chip integration as well as the integration of very small high gain arrays. The available 7 GHz of spectrum results in very high data rates, up to 5 gigabits per second to users within an indoor environment, usually within a range of 10 meters. Some press reports called this "Gi- Fi". It was developed by Melbourne University- based laboratories of NICTA (National ICT Australia Limited), Australia‘s Information and Communications Technology Research Centre of Excellence.

In 2009, the Wireless Gigabit Alliance was formed. It used the term "Wi-Gig" which avoided trademark confusion. It utilize at 5mm square chip and a 1mm wide antenna burning its less than 2milli watts of power to transmit data wirelessly over short distance. It provides many features like ease of development small from factors ,enabling the future of information management, high speed of data transfer low power consumption etc.
Features:
The Gi-fi technology allows wireless uncompressed high definition content and operates a range of 10metres, without of interference.it is chip architecture. It is highly portable and can be constructed in everywhere. Entire transmission system can be built on a cost effective single silicon chip that operates in the unlicensed 57-64 GHz spectrum band. Gi-Fi technology also enables the future of information management is easy in development with small form factor.
1. Capacity of high speed of data transfer:
The data transfer rate of Gi-fi is in gigabits/sec speed of Gi-fi is 5gbps, 10 times faster than all existing technologies providing higher data transfer rate is the main feature of gi-fi, an entire HD movie can be transmitted to a home computer or screen at the same speed.
2. Interference in Data Transfer:
It uses the 60 GHz millimeter were spectrum to transmit the data which gives the advantage are WI-FI. Wi-Fi‘s part of spectrum is increasingly crowded, phones which leads to interference and slower speeds. But the millimeter were spectrum(30 to 300 GHz) is all must an occupied And the new chip is potentially hundreds of times faster than the average home Wi-Fi technology.
3. Power consumption:
Gi-Fi technology is based on IEEE 802.15.3C and this Standard provides more security since it provides optional security in the link level and service level. Point-to-point wireless systems operating at 60 GHz have been used for many years by the intelligence community for high security communications and by the military for satellite-to-satellite communications.